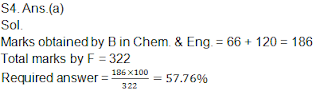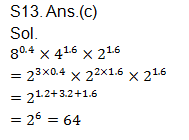Q1. Choose the odd one out:
(a) Brute force attack
(b) Virtual Reality
(c) Unethical Phreaker
(d) Keystroke logging
(e) Cross-site Scripting
S1. Ans.(b)
Sol. Except Virtual Reality all other are obvious security threats to computers and data.
Q2. The type of threats on the security of a computer system or network are ……………………..
i) Interruption ii) Interception iii) Modification
iv) Creation v) Fabrication
(a) i, ii, iii and iv only
(b) ii, iii, iv and v only
(c) i, ii, iii and v only
(d) iii, iv and v only
(e) All i, ii, iii, iv and v
S2. Ans.(c)
Sol. Except Creation all other actions performed by unauthorised and suspicious person.
i) A worm mails a copy of itself to other systems.
ii) A worm executes a copy of itself on another system.
iii) A worm cannot be spread without a human action, (such as running an infected program) to keep it going.
(a) True, False, True
(b) False, True, True
(c) True, True, False
(d) False, False, False
(e) True, True, True
S3. Ans.(c)
Sol. Worms spread from computer to computer, but unlike a virus, it has the capability to travel without any human action.
(a) Existing program files and icons disappear
(b) The CD-ROM stops functioning
(c) The web browser opens to an unusual home page
(d) Odd message or images are displayed on the screen
(e) None of these
S4. Ans.(b)
Sol. Except option (b) all others are the symptoms of a computer virus.
Q5. VIRUS stands for___________.
(a) Vital Information Resources Under Siege
(b) Viral Important Record User Searched
(c) Very Interchanged Result Until Source
(d) Very Intelligent Resources Under Search
(e) None of these
S5. Ans.(a)
Sol. VIRUS stands for Vital Information Resources Under Siege
Q6. A virus that migrates freely within a large population of unauthorized email user is called a __________.
(a) worm
(b) flame war
(c) macro
(d) plagiarism
(e) None of these
S6. Ans.(c)
Sol. A macro virus is a virus that is written in a macro language: a programming language which is embedded inside a software application (e.g., word processors and spreadsheet applications)
(a) Creeper
(b) Sasser
(c) Blaster
(d) All of the above
(e) None of these
S7. Ans.(a)
Sol. Creeper virus is a computer virus that is most commonly recognized as the first computer virus.
(a) Unique key columns do not accept duplicate values.
(b) One table can have only one unique key.
(c) By default, unique key columns accept null values unless the NOT NULL constraint is specified.
(d) The same combinations of columns should not make both unique and primary keys.
(e) None of these
S8. Ans.(b)
Sol. Since one table can have at the most one primary key to avoid duplicates in other columns of the table, unique key can be defined. We can make one or more unique keys in a single table.
(a) <H1>
(b) <H2>
(c) <H3>
(d) <H4>
(e) <H5>
S9. Ans.(d)
Sol. The text written within the H4 element has the same size as the normal plain text, whereas the text written within the H1, H2 and H3 elements are larger than the normal text. Text written within the H5 and H6 elements has smaller size than the normal text.
Q10. Which of the following HTML tags is a logical style tag?
(a) <B>
(b) <I>
(c) <SMALL>
(d) <ABBR>
(e) None of these
S10. Ans.(d)
Sol. In HTML, logical style tags specify that the enclosed text has a specific meaning, context, or usage. The <ABBR> is a logical style tag, which conveys to the Web browser that the text enclosed within this tag is an abbreviation.
(a) Data Denial-of-Service
(b) Distributed Denial-of-Service
(c) Distributed Data of Server
(d) Distribution of Data Service
(e) None of these
S11. Ans.(b)
Sol. Distributed Denial-of-Service (DDoS) attack is a type of attack that is carried out by using multiple computers. These DDoS attacks aim at targeting computer networks of an organisation, such as Digital Subscriber Line (DSL) and cable.
(a) It reduces traffic congestion.
(b) It allows prioritizing of messages.
(c) It allows broadcasting of messages.
(d) It is an inexpensive network.
(e) It is not compatible with videoconferencing.
S12. Ans.(d)
Sol. In a message-switched network, a packet containing the entire message is transmitted over the network. It is a more expensive network.
Q13. Which of the following statements is false in the context of client/server network?
(a) It is expensive to set up.
(b) It requires a specialized server.
(c) It is a slow network.
(d) It is highly secure.
(e) It is a congested network.
S13. Ans.(c)
Sol. The client/server network contains a centralised server that manages and controls all the other nodes of the network. It is expensive as it requires NOS and a specialized server system. It is highly secure and processes good speed. However, it becomes congested when more clients simultaneously request for a service to the server.
Q14. A pathway inside a computer that carries data between hardware components is called _____________.
(a) carrier signal
(b) data bus
(c) digital signal
(d) analog signal
(e) switching
S14. Ans.(b)
Sol. A data bus connects internal components to the motherboard and acts as a carrier for the data.
Q15. Which of the following is related to simplex communication?
(a) Single wire and two-sided communication
(b) Television
(c) Two-wire communication
(d) Walkie-talkie
(e) None of these
S15. Ans.(b)
Sol. Television is an example of simplex communication.